|
Google Associate Cloud Engineer Exam Page8(Dumps)
Question No:-71
|
You are using Container Registry to centrally store your company's container images in a separate project. In another project, you want to create a Google Kubernetes Engine (GKE) cluster. You want to ensure that Kubernetes can download images from Container Registry.
What should you do?
1. In the project where the images are stored, grant the Storage Object Viewer IAM role to the service account used by the Kubernetes nodes.
2. When you create the GKE cluster, choose the Allow full access to all Cloud APIs option under 'Access scopes'.
3. Create a service account, and give it access to Cloud Storage. Create a P12 key for this service account and use it as an imagePullSecrets in Kubernetes.
4. Configure the ACLs on each image in Cloud Storage to give read-only access to the default Compute Engine service account.
|
Answer:-3. Create a service account, and give it access to Cloud Storage. Create a P12 key for this service account and use it as an imagePullSecrets in Kubernetes.
|
|
Question No:-72
|
You deployed a new application inside your Google Kubernetes Engine cluster using the YAML file specified below.
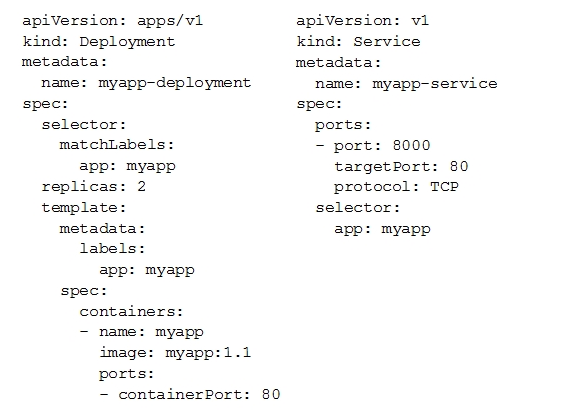 You check the status of the deployed pods and notice that one of them is still in PENDING status:
You check the status of the deployed pods and notice that one of them is still in PENDING status:
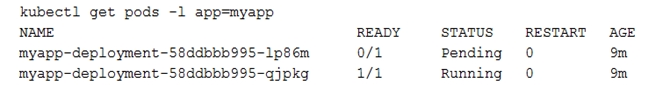 You want to find out why the pod is stuck in pending status. What should you do?
You want to find out why the pod is stuck in pending status. What should you do?
1. Review details of the myapp-service Service object and check for error messages.
2. Review details of the myapp-deployment Deployment object and check for error messages.
3. Review details of myapp-deployment-58ddbbb995-lp86m Pod and check for warning messages.
4. View logs of the container in myapp-deployment-58ddbbb995-lp86m pod and check for warning messages.
|
Question No:-73
|
You are setting up a Windows VM on Compute Engine and want to make sure you can log in to the VM via RDP. What should you do?
1. After the VM has been created, use your Google Account credentials to log in into the VM.
2. After the VM has been created, use gcloud compute reset-windows-password to retrieve the login credentials for the VM.
3. When creating the VM, add metadata to the instance using 'windows-password' as the key and a password as the value.
4. After the VM has been created, download the JSON private key for the default Compute Engine service account. Use the credentials in the JSON file to log in to the VM.
|
Answer:-4. After the VM has been created, download the JSON private key for the default Compute Engine service account. Use the credentials in the JSON file to log in to the VM.
|
|
Question No:-74
|
You want to configure an SSH connection to a single Compute Engine instance for users in the dev1 group. This instance is the only resource in this particular Google Cloud Platform project that the dev1 users should be able to connect to. What should you do?
1. Set metadata to enable-oslogin=true for the instance. Grant the dev1 group the compute.osLogin role. Direct them to use the Cloud Shell to ssh to that instance.
2. Set metadata to enable-oslogin=true for the instance. Set the service account to no service account for that instance. Direct them to use the Cloud Shell to ssh to that instance.
3. Enable block project wide keys for the instance. Generate an SSH key for each user in the dev1 group. Distribute the keys to dev1 users and direct them to use their third-party tools to connect.
4. Enable block project wide keys for the instance. Generate an SSH key and associate the key with that instance. Distribute the key to dev1 users and direct them to use their third-party tools to connect.
|
Question No:-75
|
You need to produce a list of the enabled Google Cloud Platform APIs for a GCP project using the gcloud command line in the Cloud Shell. The project name is my-project. What should you do?
1. Run gcloud projects list to get the project ID, and then run gcloud services list --project <project ID>.
2. Run gcloud init to set the current project to my-project, and then run gcloud services list --available.
3. Run gcloud info to view the account value, and then run gcloud services list --account <Account>.
4. Run gcloud projects describe to verify the project value, and then run gcloud services list --available.
|
Answer:-1. Run gcloud projects list to get the project ID, and then run gcloud services list --project <project ID>.
|
|
Question No:-76
|
You are building a new version of an application hosted in an App Engine environment. You want to test the new version with 1% of users before you completely switch your application over to the new version. What should you do?
1. Deploy a new version of your application in Google Kubernetes Engine instead of App Engine and then use GCP Console to split traffic.
2. Deploy a new version of your application in a Compute Engine instance instead of App Engine and then use GCP Console to split traffic.
3. Deploy a new version as a separate app in App Engine. Then configure App Engine using GCP Console to split traffic between the two apps.
4. Deploy a new version of your application in App Engine. Then go to App Engine settings in GCP Console and split traffic between the current version and newly deployed versions accordingly.
|
Answer:-4. Deploy a new version of your application in App Engine. Then go to App Engine settings in GCP Console and split traffic between the current version and newly deployed versions accordingly.
|
|
Question No:-77
|
You need to provide a cost estimate for a Kubernetes cluster using the GCP pricing calculator for Kubernetes. Your workload requires high IOPs, and you will also be using disk snapshots. You start by entering the number of nodes, average hours, and average days. What should you do next?
1. Fill in local SSD. Fill in persistent disk storage and snapshot storage.
2. Fill in local SSD. Add estimated cost for cluster management.
3. Select Add GPUs. Fill in persistent disk storage and snapshot storage.
4. Select Add GPUs. Add estimated cost for cluster management.
|
Question No:-78
|
You are using Google Kubernetes Engine with autoscaling enabled to host a new application. You want to expose this new application to the public, using HTTPS on a public IP address. What should you do?
1. Create a Kubernetes Service of type NodePort for your application, and a Kubernetes Ingress to expose this Service via a Cloud Load Balancer.
2. Create a Kubernetes Service of type ClusterIP for your application. Configure the public DNS name of your application using the IP of this Service.
3. Create a Kubernetes Service of type NodePort to expose the application on port 443 of each node of the Kubernetes cluster. Configure the public DNS name of your application with the IP of every node of the cluster to achieve load-balancing.
4. Create a HAProxy pod in the cluster to load-balance the traffic to all the pods of the application. Forward the public traffic to HAProxy with an iptable rule. Configure the DNS name of your application using the public IP of the node HAProxy is running on.
|
Question No:-79
|
You need to enable traffic between multiple groups of Compute Engine instances that are currently running two different GCP projects. Each group of Compute Engine instances is running in its own VPC. What should you do?
1. Verify that both projects are in a GCP Organization. Create a new VPC and add all instances.
2. Verify that both projects are in a GCP Organization. Share the VPC from one project and request that the Compute Engine instances in the other project use this shared VPC.
3. Verify that you are the Project Administrator of both projects. Create two new VPCs and add all instances.
4. Verify that you are the Project Administrator of both projects. Create a new VPC and add all instances.
|
Answer:-
2. Verify that both projects are in a GCP Organization. Share the VPC from one project and request that the Compute Engine instances in the other project use this shared VPC.
|
|
Question No:-80
|
You want to add a new auditor to a Google Cloud Platform project. The auditor should be allowed to read, but not modify, all project items.
How should you configure the auditor's permissions?
1. Create a custom role with view-only project permissions. Add the user's account to the custom role.
2. Create a custom role with view-only service permissions. Add the user's account to the custom role.
3. Select the built-in IAM project Viewer role. Add the user's account to this role.
4. Select the built-in IAM service Viewer role. Add the user's account to this role.
|
|